Cleverly Repair Large Corrupted Files with BitTorrent Client Checksum Hash Scans
I admit, I have a very fast broadband connection at home. My link speed is more than 6 Mbps. You’d think I can’t complain. But there are some files that seem to download for an eternity. Take, for instance, the Windows Vista Beta. On my connection, that 4 GB bloatware *.ISO mammoth took about two hours to download. Even, when I used DownThemAll!, it took about an hour and a half! That is way too much time to spend for downloading.
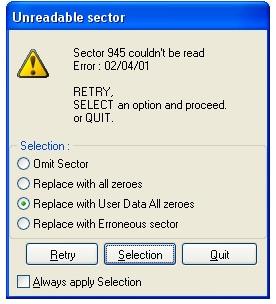 Corrupted *.ISO Image File
Corrupted *.ISO Image File
When I was writing one of my most recent articles on free T-Mobile Hotspots and Microsoft Windows Beta virtualization, I needed a copy of Windows Vista Beta. I wasn’t exactly looking forward to another 2-hour wait of download time. So, I checked my stack of burned CDs and DVDs for an old copy. To my good luck, I found the original copy of Vista. I just had to rip it to my hard drive for faster virtualization. Unfortunately, there were about 5 unrecoverable disk sector read errors. “Maybe,” I rationalized, “Vista won’t really care if there are just a couple of corrupted data bytes. Besides, I just need it for one small task.” I was wrong. The Windows Vista installation program actually performs a corruption test to make sure everything is set before actually proceeding with the installation.
To think that 4 tiny sectors in the DVD hampered my schemes of exploiting T-Mobile! Would I have to redownload the ISO image online to continue with my plans? No! Fortunately, I found a forum thread from Locker Gnome (bless Chris Pirillo) that helped deal with corrupted Vista ISO image error 80070241 code. The solution was simply ingenious!
BitTorrent Checksum Hash Scans
To repair large corrupted files, you have to understand how hash scans and torrents work. A *.torrent file contains two important pieces of information, the torrent tracker address and the hash key. The address of the torrent tracker contains all the IP addresses that have pieces of the desired file. The torrent client downloads data segments of the desired file from different IP addresses referred to by the tracker. Depending on the size of the desired file (in my case 4 GB), there can be hundreds of file segments to download. After each segment is downloaded, the torrent client uses the hash key to validate the data so each file segment is exactly the same as the one in the original file. This ensures that any corrupted data, dummy data, or malicious data isn’t mixed into the final product.
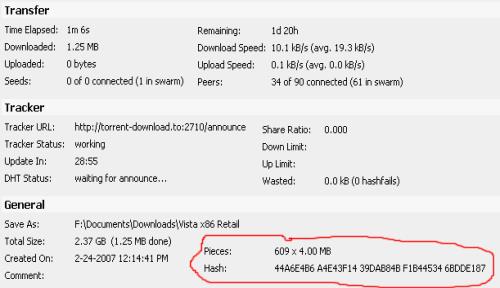
Repair Files with the Checksum
This hash check occurs several times in a torrent client but the most important time, in this case, is when the program starts up. Before clients begin to download, upload, or seed a torrent, the programs do a complete hash check of the data already downloaded and available. With large corrupted files, you can take advantage of this hash check.
- Just find a torrent of the exact file in The Pirate Bay, ISOHunt, or TorrentSpy and download it for about a minute.
- Then, stop and close the client.
- Replace the torrent data file with the corrupted file.
- Reopen the client and start the download. The client will perform a hash MD5 check on the current data to see what file segment downloads are necessary. If you correctly found a torrent of the exact file, the client will redownload the segment of the corrupted data and rebuild the file. In the end, you should be good to go!
Cons
There are a couple of caveats for using this method to repair corrupted files.
- It’s kinda shady. Depending on the file, legality of torrenting may be questionable.
- You have to find a torrent of the exact file.
- The torrent tracker must have some IP addresses participating. You may find the torrent of the exact file but that torrent may also be dead.
Leave a comment on your experience with this method or post any other suggestions!

 Subscribe by RSS Feed
Subscribe by RSS Feed Stumble it!
Stumble it! Furl This!
Furl This! Reddit!
Reddit!
October 28th, 2008 at 5:21 pm
Just thought I\’d mention my rather awesome experience with this trick. Three years or ago, I\’d downloaded the Doom 3 demo while at university, knowing that my punily-spec\’d laptop wouldn\’t manage it. But I was going home for the weekend where my far beefier desktop resided. So I pulled all the music off my 1GB (spinning disk) mp3 player and shoved it on. When I got home I copied it to the Windows desktop and was horrified to find that corruption errors stopped it from unpacking. (Quite predictable, given the medium). So I found another torrent, lazily saved it to the desktop too, and watched in amazement as it jumped to 99% and completed within a few seconds.
February 11th, 2009 at 9:44 pm
yes this is a very awesome trick to recover say, a couple files in a huge collection of a torrent. really cool stuff.
April 6th, 2009 at 11:57 pm
Torrenting a file you have already legally downloaded should be legal – the torrenting technology itself is legal, it’s only when you download content without the authors’ permission that it becomes illegal.
June 4th, 2009 at 6:10 am
i am interest each & every recovery files, folder and other useful software, please send the detial at the earliest
November 17th, 2009 at 4:44 pm
Ingenious and pefectly valid procedure. BT downloads vs. direct downloads are preferable for this very reason. MD5 or any other checksum is irrelevant if the filed has been DLed via BT.
December 28th, 2009 at 10:21 am
wincrc, or
filerepair, (http://filerepair.sourceforge.net/) or
par2, or
winrar, recovery record.(2-10%)
winrar, recovery volume (rev)
bittorrent is great.
but filerepair would be greater if it had more features, integrating a recovery record, or using MD5/CRC to reconstruct file-blocks.
msg me at ICQ:593407940
April 15th, 2010 at 1:30 pm
TY so much u helped a stoner put down the mouse and pick the bong back up ty ty ty ty
im hopeless at computers and didnt wana download 8 gigs again this way i only had to download 50 kbs
tytytytyty
August 5th, 2010 at 6:19 pm
Just as a (very) minor note, the hashing system uses SHA-1, not MD5 (very, very rare).
http://en.wikipedia.org/wiki/Torrent_file
September 30th, 2013 at 1:54 am
THB Bury9 to many more such as THB Bury 9068, 9058,
9060 and along with these a few more. The babies are born with no
fur, fused toes, and closed eyes and ears.
The forts that most of the parents choose are also equipped with
the optional Built-in Picnic Table for visiting and snacks, tea, coffee, shakes, etc.
October 14th, 2013 at 2:54 pm
Unquestionably imagine that that you said. Your favourite justification seemed to be at the internet thhe simplest factor to take into account of.
I say to you, I definitely get irked at the same time as other folks think
about worrfies that they plainly don’t recognize about. You managed to hit
the nail upon the top and also outlined out the whole thing with
no need side effect , people could take a signal. Will probably be
back to get more. Thanks
January 1st, 2014 at 12:53 am
The particular tools and techniques used in a business succession plan will vary based on
the goals and objectives of the four groups affected by the plan: the senior generation business owner, the junior generation family members involved in the business, key non-family employees, and family members not
involved in the business. re in the market for a new family
hatchback, you probably won. Would you like your family to spend
more time together as a family.
January 1st, 2014 at 2:32 am
Need for Speed: Rivals mettra en vedette un jeux similaire à un besoin de 2010 Need for Speed: Hot Pursuit titre dans la
franchise Need for Speed avec des voitures exotiques et de la police poursuites à haute vitesse.
Les joueurs prennent le rôle d’un coureur ou un flic, avec de chaque côté de la loi offrant son propre ensemble de défis, les risques et les récompenses.
Rivals mettra en vedette onze gadgets évolutifs
tels que les PGE, ondes de choc et la possibilité de faire appel à des barrages routiers.
Le jeu se déroule dans le une ville nomme ‘Redview County’, une zone de monde ouvert qui est l’hôte de déchets entre police et aux voleurs.
Le monde ouvert mettra en vedette une structure similaire
à un besoin de 2012 for Speed: Most Wanted, avec plusieurs sauts, des pièges de vitesse et les voitures à débloquer.
January 1st, 2014 at 2:35 am
It’s very simple to find out any matter on web as compared to books, as I found
this piece of writing at this website.
January 1st, 2014 at 4:45 am
When it will come to figuring out all the ins and outs of a video game|specifically the
types on your telephone|you could commit thousands of several hours on conclude
striving to beat it this is why Candy Crush Saga Live Instrument 3.eight.5 was created!
For you gamers to consider gain of all the specific characteristic this tool offers.
Not only you will advantages from all these characteristics but you will also support your self defeat each and every level the frustrated you for a although.
No much more waiting hrs to get life or have a limited quantity
of boosters. Now every thing you want has been
provided in this instrument and suitable with Fb|Apple Products (Ipod|Ipad|Iphones) and
Android telephones also.
February 3rd, 2014 at 4:14 pm
Thank you for every other fantastic post. Where else could
anyone get that kind of info in such a perfect method
of writing? I have a presentation subsequent week, and I’m on the
look for such information.
March 11th, 2014 at 3:49 am
It’s very simple to find out any topic on
web as compared to books, as I found this piece of
writing at this site.
March 31st, 2014 at 8:43 am
Nice post. I used to be checking constantly this blog and I’m impressed!
Extremely helpful information specifically the ultimate
part 🙂 I take care of such info much. I was seeking this certain info
for a long time. Thanks and best of luck.
April 11th, 2014 at 5:29 am
It’s an remarkable paragraph in support of all the internet visitors; they will
take benefit from it I am sure.
April 12th, 2014 at 12:49 am
This info is invaluable. How can I finbd out more?
April 22nd, 2014 at 12:39 am
I needed to thank you for this excellent read!! I absolutely
enjoyed every bit of it. I have got you bookmarked to look at
new stuff you post…
Stop by my blog … Need for Speed Most Wanted Hack Download; http://www.pinterest.com,
April 29th, 2014 at 11:52 am
Wow that was odd. I just wrote an extremely long comment but after I clicked submit my comment didn’t
show up. Grrrr… well I’m not writing all that
over again. Anyway, just wanted to say fantastic blog!
Also visit my blog post … Gt Racing 2 Hack Download
April 30th, 2014 at 7:14 pm
Hey just wanted to give you a brief heads up and let you know a few of the images aren’t loading properly.
I’m not sure why but I think its a linking issue.
I’ve tried it in two different web browsers and both show the
same outcome.
Feel free to visit my web blog … CSR Clasics Hack Download (Dawna)